|
|
|
|
|
IAR C-SPY, Debugger & MISRA Checker
C-SPY® Integration
Graphical state machine debugging on hardware
The IAR C-SPY IDE and Debugger is an integrated part of the IAR Embedded Workbench toolsuite. It is available for a wide range of microcontrollers and supports many on-target debug options and interfaces. The C-SPY debugger is also Task-aware for a many Real-Time Operating Systems (RTOS).
The unique integration between C-SPY Debugger in IAR Embedded Workbench® and IAR visualSTATE® makes it possible to see what is going on at the state machine design level at the target device.
- View received event triggers, executed action functions and the resulting global system state directly in C-SPY.
- Set state machine breakpoints directly at a state or a set of states, to stop execution once the specified states become active.
- Get animation directly in the design diagrams, to follow execution on an even higher level.
- No need to write support code in the form of communications routines
etc—just compile and go! There is no need for extra communications ports
etc—C-SPY handles all communication needed.
- Available for the vast majority of available IAR Embedded Workbench solutions for 8-, 16-, and 32-bit architectures.
- Choose between a number of different execution modes, to maximize feedback or real-time performance while debugging.
- On-Target debugging using our range of Emulators & Trace systems
Standard MISRA Checker
The MISRA C checker is completely integrated with IAR C/C++ Compiler. From IAR Embedded Workbench, you can control which MISRA C rules are checked; the settings will be used for both the compiler and the linker.
The implementation of the MISRA C rules does not affect code generation, and has no significant effect on the performance of IAR Embedded Workbench. The compiler and linker only generate error messages, they do not actually prevent you from breaking the rules you are checking for. You can enable or disable individual rules for the entire project or at file level. A log is produced at compile and link time, and displayed in the Build Message window of the IAR Embedded Workbench IDE. This log can be saved to a file, as described in the IAR Embedded Workbench User Guide.
Note: MISRA C checker is included free-of-charge in standard editions of IAR Embedded Workbench products. Currently MISRA-C:2004 support is available in target V850, 78K and AVR32. MISRA support on the other targets will be implemented with new releases.
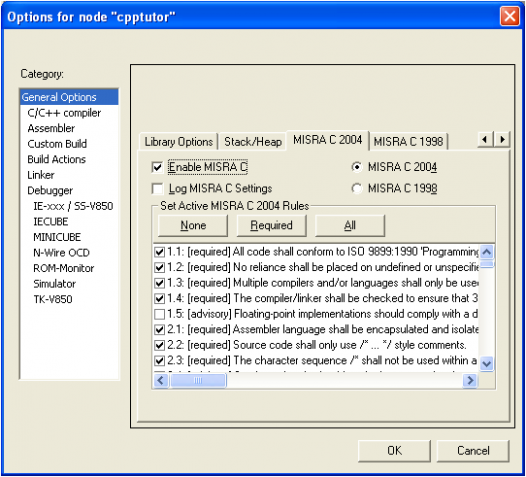
A message is generated for every deviation from a required or advisory rule, unless you have disabled it. Each message contains a reference to the MISRA C rule deviated from.The format of the reference is as in the following error message:
Error[Pm088]: pointer arithmetics should not be used (MISRA C 2004 rule 17.4)
Note: The numbering of the messages does not match the rule numbering.
For each file being checked with MISRA C enabled, you can generate a full report ontaining a list of:
MISRA C compliance
To claim compliance with the MISRA C guidelines for your product, you must demonstrate that:
-
A compliance matrix has been completed demonstrating how each rule is enforced.
-
All C code in the product is compliant with the MISRA C rules or subject to documented deviations.
-
A list of all instances where rules are not being followed is maintained, and for each instance there is an appropriately signed-off documented deviation.
-
You have taken appropriate measures in the areas of training, style guide, compiler selection and validation, checking tool validation, metrics, and test coverage, as described in section 4.2 of Guidelines for the Use of the C Language in Critical Systems.
For additional information, please feel free to contact Gerard Fianen at Indes - IDS B.V.
|
|
|
|

















