|
|||||||||||||||||||||||||||||||||||||||||||||||||
| Nederlands | French |
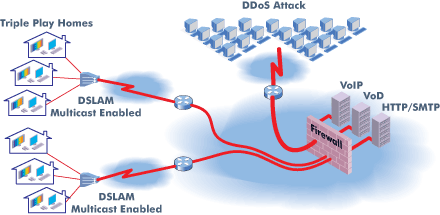
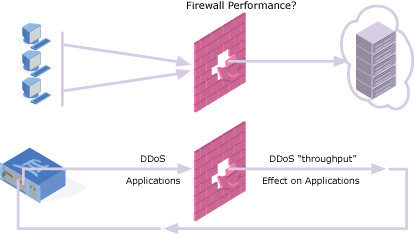
Security PerformanceIP networks and protocols are susceptible to security attacks through malicious content such as viruses, worms and distributed denial of service (DDoS) attacks, along with the proliferation of Spam. Establishing performance limitations for converged IP services like Triple Play is critical for high quality performance applications such as IPTV, VoD and VoIP. In most cases network architects have included firewalls, Intrusion detection and prevention applications into their network infrastructure. Understanding how these elements affect time sensitive applications such as voice and video is a real concern.
Today, cyber crime is widespread. Denial of Service Attacks, as the name implies attempt to block normal services by tying up the victims resources. A very basic attack is a GET request for a web page, but scaled to thousands of requests per second. Within fractions of a second buffers can become flooded, CPU performance exhausted etc., leading to legitimate application requests becoming extremely slow or worse case, ignored. This leads to very poor user quality of experience.
diversifEye™ comprehensively tests converged IP network architectures for weaknesses in security and importantly provides a unique ability to determine the effects of attacks on both overall network quality of service and quality of individual experience. diversifEye™ unique per flow architecture not only enables emulation of regular client side and server side applications, but also provides for the insertion of malicious attack content onto the network and into IP traffic streams. diversifEye™ generates a real world traffic mix of genuine and malicious content containing IPTV streams, VoD requests, VoIP calls, web or mail downloads in unfavorable conditions along with email virus/worm attacks, real spam generation, DDoS attacks on servers, malicious exploitation of protocols e.g. IGMP weaknesses, channel change requests and membership reports. Generate a traffic mix of genuine and malicious content containing IPTV streams, VoD requests, VoIP calls, web or mail downloads in unfavorable conditions with virus/worm proliferation, denial of service attacks on servers, malicious exploitation of protocols e.g. IGMP weaknesses, channel change requests and membership reports.
Discover more about testing Security with diversifEye™ Testing the Performance of Secure IP Networks here>>
|
|
 |
|||||||
 |
 |
 |
 |
||||